Cryptika quickly earned a reputation for firsts. We were the first in region to provide our business customers with industry’s first integrated, end-to-end security operations and response services
An integrated cybersecurity and a managed services provision firm. Cryptika comprises a comprehensive team of experts and thought leaders. Our scope of work includes everything from design, implementation of governance, risk, compliance and business continuity frameworks. We are helping our customers to thrive in ever changing business and highly competitive business environment, through our bottom-up Innovation, backed up by strength of delivering high-end and complex engineering engagements.
Cryptika quickly earned reputation for firsts. We were the first to provide our business customers with industry's first integrated, end-to-end security operations and response services. Assisting our customers evaluating their IT related business risks, building and improving IT security strategies, designing infrastructures, implementing international security standards such as the ISO 27k ISMS, PCI-DSS, and SWIFT CSP. Cryptika goes beyond business level and management systems, where we evaluate and audit our customers environments at the IT systems, infrastructure and business applications level by providing penetration testing, vulnerabilities assessments, security architecture review services.
We’re delivering a new approach in cybersecurity, purposely designed to protect your organization from the most advanced cyber-attacks. Our pioneering approach to threat hunting and response has been rigorously tested and proven by highly regarded third-party industry analysts.
We believe standing up for our values is the highest form of honor. We assist our customers in operating and maintaining their IT assets and applications with full discretion, prudence and diligence - both financial and technical. Our strength is in our ability to carter to our clients’ varied needs and provide a highly competitive procurement management service. Our aim is to keep you at the forefront of technology securely and economically.
Whether you are looking for advice, testing or auditing services, it is our job as information risk, security and compliance specialized firm to keep our customers protected in today's dynamic risk environment. Our elite team, experience and proven approach keeps you protected with future-proofed advice delivered in plain English. By thinking outside the box, and keeping up to date with all the latest industry developments, we ensure we keep you one step ahead of the cyber threats and vulnerabilities.
Vulnerabilities Assessment & Penetration Testing (VAPT)
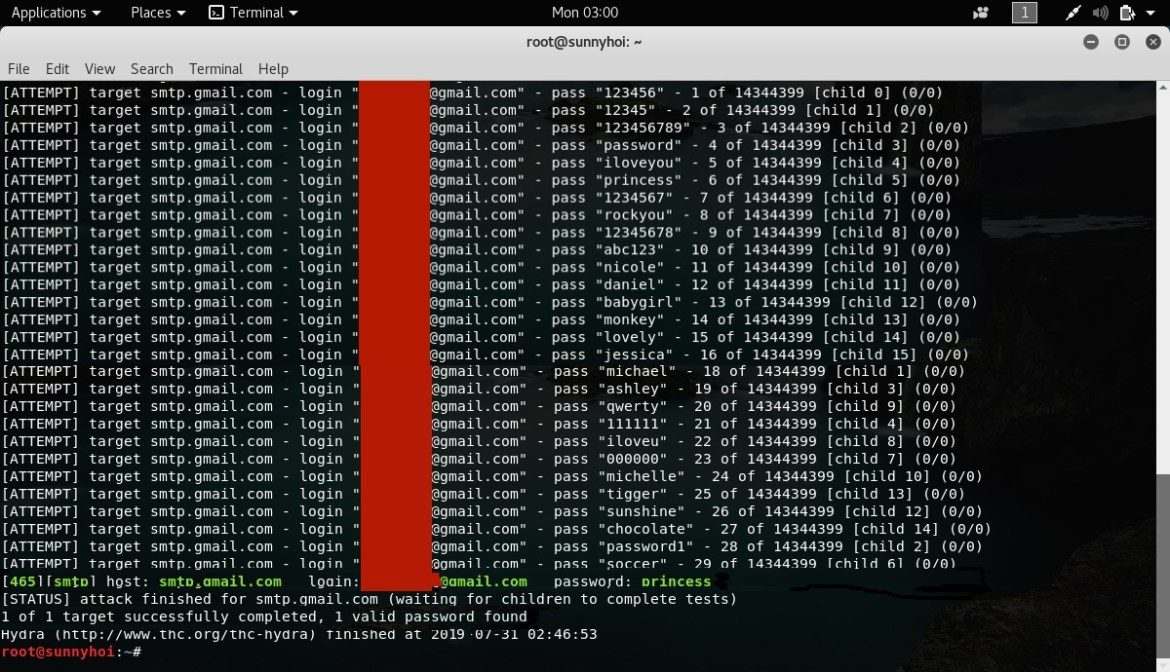
VAPT helps protecting businesses by exposing weaknesses that provide an alternative route to sensitive data. Penetration Testing aim to identify hidden security issues that exist as a result of insecure applications development and/or configuration practices in the design, codes, operating systems, network and publishing tools. Our VAPT generally includes:
Automated Scan: Conducting thorough information security vulnerabilities scanning for servers hosting and running business applications; exploring security vulnerabilities and gaps in the network, operating systems all the way to up to business applications
Manual Review: Assessing business applications for flaws and vulnerabilities, such as XSS (cross-site scripting), SQL Injection, SSRF, CSRF, IDOR, XML Injection, CRLF and many other critical vulnerabilities along the ten most critical application security risks announced by OWASP Top 10 2021 (latest release)
Planning PT: Filtering results excluding false positives, and identifying exploitable vulnerabilities. Analyzing, setting priorities and modeling what's left over. Developing attack scenarios for each
Exploitation Attempt: Coordinating regarding schedule/methods of applying attack scenarios on targeted environment, where evidences of the penetration (such as a screen shot) is collected for reporting purposes
Cryptika testing services gives you immediate, global visibility into where your IT systems might be vulnerable to the latest cyber threats and how to protect them. It helps you to continuously secure your IT infrastructure and comply with internal policies and external regulations.
We’re assisting our customers evaluating their IT related business risks, building and improving IT security strategies, designing infrastructures, implementing international security standards including the ISO 27k ISMS, PCI-DSS, and SWIFT CSP
Penetration testing companies in dubai, penetration testing companies in UAE penetration testing companies in saudi arabia penetration testing in riyadh penetration testing companies in riyadh penetration testing vendors in middle east penetration testing company in dubai cyber security companies in gulf region cyber security company in dubai in uae service provider in dubai in riyadh in uae in ksa in kuwait
cybersecurity penetration testing companies in saudi arabia penetration testing in riyadh penetration testing companies in riyadh penetration testing vendors in middle east penetration testing company in dubai cyber security companies in gulf region cyber security company in dubai in uae service provider in dubai in riyadh in uae in ksa in kuwait
penetration testing companies in saudi arabia penetration testing in riyadh penetration testing companies in riyadh penetration testing vendors in middle east penetration testing company in dubai cyber security companies in gulf region cyber security company in dubai in uae service provider in dubai in riyadh in uae in ksa in kuwait
Governance, Risk and Compliance (GRC) Consulting
Cryptika GRC services provides a strategic approach for organization's overall governance, enterprise risk management and compliance with local regulations, and international standards. We provide you with the knowledge and tools to comply with many common regulations, standards, and compliance mandates, including:
ISO27k | PCI-DSS | NIST | GDPR | SWIFT CSP, CSCF | ECC | ISR | SIA | CSF
Saudi Arabia’s National Cybersecurity Authority (NCA): Essential Cybersecurity Controls (ECC)
Saudi Arabia's Communication and Information Technology Commission (CITC): Cybersecurity Regulatory Framework (CRF)
Saudi Arabian Monetary Authority (SAMA): Cyber Security Framework (CSF)
UAE National Electronic Security Authority (NESA): Information Assurance Standard (SIA)
Dubai Electronic Security Center: Information Security Regulation v2 (ISR)
Central Bank of Jordan (CBJ): Cyber Security Framework (CSF)
GRC consulting services from Cryptika starts by establishing good comunication with top and mid level management to understand your business and implement the right framework for your own needs
Think of GRC as a structured approach to aligning IT with overal business goals, keeping effective management of risks and meeting compliance requirements
Governance: A framework meant to ensure organization's IT investments support business objectives, and taking their stakeholders and staff’s best interests into account.
Risk Management: A forecast and evaluation of risks, and identification of procedures to avoid or minimize their impact.
Compliance: A program implementation to ensure that organizations are aware of and take steps to comply with relevant laws, policies and regulations.
penetration testing companies in saudi arabia penetration testing in riyadh penetration testing companies in riyadh penetration testing vendors in middle east penetration testing company in dubai cyber security companies in gulf region cyber security company in dubai in uae service provider in dubai in riyadh in uae in ksa in kuwait
penetration testing companies in saudi arabia penetration testing in riyadh penetration testing companies in riyadh penetration testing vendors in middle east penetration testing company in dubai cyber security companies in gulf region cyber security company in dubai in uae service provider in dubai in riyadh in uae in ksa in kuwait
Improving business performance, turning risks into opportunities, developing strategies and enhancing value are at the core of what we do for our customers.
Risk assessments / IT control benchmarking
IT audit
IT & IS policies & procedure manual
Disaster recovery planning, implementation & testing
A successful, well-implemented information security strategy is essential for the success of any modern business. We want to help you reach your goals.
Determine and assess your SOC maturity
Threat landscape rapidly evolves, where Security Operations Centers (SOC) are in the front line of defense, they need to be effective, mature and capable of detecting, investigating and responding to complex and persistent attacks.
We measure, assess and evolve the maturity of your SOC based on a proven capability maturity framework. In our assessment, we apply real world attack scenarios to determine the overall defense maturity and to gain insights on how to improve the effectiveness and efficiency.
Features:
Operational assessments for people, process, and technology
SIEM use-case development
Splunk, ArcSight, and Qradar Expertise
Review of incident playbooks and respone procedures (SOPs)
Blue team assessments
Simulated incidents with custom software to test SIEM implementation
SOC Maturity Assessment is a way to exactly determine where your cyber posture stands, how much you have ROI at the SOC you have, how effective it is, and how much cyber resilient it is.
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
Penetration Testing Dubai
Penetration Test Dubai
Penetration Testing UAE
Penetration Test UAE
Cybersecurity Dubai
Cyber Security Dubai
CyberSecurity UAE
Cyber Security UAE
Penetration Testing Riyad
Penetration Test KSA
Penetration Test Saudi
Penetration Test Kuwait
Penetration Test Qatar
Penetration Testing KSA
Penetration Test Amma
Cybersecurity Riyad
Cyber Security Riyad
CyberSecurity KSA
Cyber Security KSA
Cryptika Cyber security is a fully integrated cyber security and managed services provider comprise a comprehensive team of experts and thought leaders.
Cryptika Cyber security Company scope of work includes everything from design, implementation and procurement of high tech IT infrastructure to cyber security, cyber surveillance and full IT managed services SWIFT CSP CSCF
Cryptika Cyber security Vendor based in Dubai, UAE, United Arab Emirates
Cryptika Cryptica Based in Amman in Jordan Cryptika is a cyber security and IT security service provider providers company companies and a vendor vendors of antivirus Cryptic provider Cryptik penetration testing penetration testers tester test penetration pentest pentesting hacking ethical hackers ethical hacker hacking SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority (NCA): Essential Cybersecurity Controls (ECC)
Saudi Arabia's Communication and Information Technology Commission (CITC): Cybersecurity Regulatory Framework (CRF)
Saudi Arabian Monetary Authority (SAMA): Cyber Security Framework (CSF)
UAE National Electronic Security Authority (NESA): Information Assurance Standard (SIA)
Dubai Electronic Security Center: Information Security Regulation v2 (ISR)
Central Bank of Jordan (CBJ): Cyber Security Framework (CSF) SOC Managed SOC Consulting Consultants consultant SWIFT CSP CSCF Information security IT Security IT Governance Risk management best practices GRC SIEM SOAPA Information security assurance cybersecurity assurance it assurance security assurance availability assurance business continuity assurance digital forensics DFIR change management compliance and audit data leakage prevention Cyber Security Next-Generation penetration testers testing test penetration Antivirus Cybersecurity NGAV SAST DAST IAST Threat Hunting Threat Hunt NG AV
Cryptika Cyber security Vendor based in Riyadh, KSA, Saudi Arabia
Antivirus Cybersecurity NGAV SAST DAST IAST Threat Hunting Threat Hunt NG AV Intelligence threat intelligence Security operations center Governance compliance risk
DAST SAST Jordan SAST SWIFT CSP CSCF service in jordan SAST jordan DAST Jordan SAST Professional
Netsparker Jordan Netsparker partners in middle east fortify acunetix
Cryptika Cyber security Provider based in Dubai, UAE, United Arab Emirates
LastLine Antivirus Vendor top Antivirus Companies Solve Ransomware Restore data encrypted data Stop Ransomware fabric solutions WannaCry EDR NGAV Companies EDR dast, sast, code review, dynamic application security testing, static application security testing, static code analysis
Cryptika Cyber security Provider based in Riyadh, KSA, Saudi Arabia
Netsparker Jordan Netsparker partners in middle east fortify acunetix information security manager SWIFT CSP CSCF management GDPR Indecent response handling lead implementer auditor Streaming Prevention Our Company's address is in Amman red team redteam threat hunter responder SOC analyst CyberSec 22001 ISO 2000289 VAPT Jordan VAPT VA PT VAPT services VAPT service VAPT Professional
Cryptika Cyber security Firm based in Dubai, UAE, United Arab Emirates
penetration testing and vulnerability assessment, Vulnerability Assesment and Penetration Testing (VAPT) Service. This service enable to find vulnerabilities in network devices, application and using security
Cryptika Cyber security Firm based in Riyadh, KSA, Saudi Arabia
Top Penetration Testers in Middle East Penetration Testing Companies in UAE Penetration Testing Providers in Dubai Penetration Testing Consulting Firms in Saudi Arabia KSA Riyadh
Cryptika Cyber security Team
Top 5 Penetration Testing Providers in Dubai Cryptika UAE Cryptika Abu Dhabi Cryptika United Arab Emirates Cryptika Top 10 Penetration Testing test Companies in Middle East Cryptika Top VAPT Providers in Dubai Abu Dhabi UAE United Arab Saudi Arabia KSA Riyadh Amman Jordan Address: Dubai Sheikh Zayed Street
Cryptika Cyber security Partner Dubai, UAE, United Arab Emirates
dast, sast, code review, dynamic application security testing, static application security testing, static code analysis, PT, dast, sast, vapt, va,
it security jordan cyber security jordan pentester penetration testers jordan
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
Cryptika cybersecurity Head Quarter HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Cryptika Cyber security Partner based in Riyadh, KSA, Saudi Arabia
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
ASVS DAST Application Security Verification Standard Companies in Dubai UAE Middle East SOC Maturity Test DDoS Stress Test Testing Phishing Testing APT REDTEAMING Red-Teaming Security Architecture High Level Design Review CyberSecurity Architect in Dubai Cryptika
Cryptika Cyber security Companies Dubai, UAE, United Arab Emirates
Security Architecture Review Architect HLD High Level Design Review Configuration Review Config Security Configuration
Cryptika Cyber security Companies Riyadh, KSA, Saudi Arabia
Security Architecture Review Architect HLD High Level Design Review Configuration Review Config Security Configuration VAPT Providers top infosec information security
Cryptika Cyber security Vendors Dubai, UAE, United Arab Emirates
dos attack zero day zeroday zero-day 0day SWIFT CSP CSCF vulnerabilities vulnerability assessment management IT Security center forum comession department Cryptika SOC Cb Defense is certified to replace antivirus meet PCI and HIPAA ISO 27001 COBIT ITIL compliance requirements and protect information in the cloud. PCI-DSS Certificate lead implementer auditor That's why Cb Defense is trusted SWIFT CSP CSCF by leading analysts and industry associations Cryptica Crypto Cyber Intelligence cyber detective Cybereason antiransomware ransomware protection zero-day attacks protection Cb Response Protection Cb Defense is proven to replace AV with better protection increased visibility and an easy experience that keeps users productive. Backed by world-class threat research and customer service our customers know their security comes first. UEBA UBEA Beyond the Hype
Cryptika Cyber security Vendors Riyadh, KSA, Saudi Arabia
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority (NCA): Essential Cybersecurity Controls (ECC)
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Saudi Arabia's Communication and Information Technology Commission (CITC): Cybersecurity Regulatory Framework (CRF)
Saudi Arabian Monetary Authority (SAMA): Cyber Security Framework (CSF)
UAE National Electronic Security Authority (NESA): Information Assurance Standard (SIA)
Dubai Electronic Security Center: Information Security Regulation v2 (ISR)
Central Bank of Jordan (CBJ): Cyber Security Framework (CSF)
Cryptika Cyber security Providers Dubai, UAE, United Arab Emirates
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority (NCA): Essential Cybersecurity Controls (ECC)
Saudi Arabia's Communication and Information Technology Commission (CITC): Cybersecurity Regulatory Framework (CRF)
Saudi Arabian Monetary Authority (SAMA): Cyber Security Framework (CSF)
UAE National Electronic Security Authority (NESA): Information Assurance Standard (SIA)
Dubai Electronic Security Center: Information Security Regulation v2 (ISR)
Central Bank of Jordan (CBJ): Cyber Security Framework (CSF)
Cryptika Cyber security Providers Riyadh, KSA, Saudi Arabia
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Dubai, UAE, United Arab Emirates
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Riyadh, KSA, Saudi Arabia
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Teams
Cryptika Cyber security Partners Dubai, UAE, United Arab Emirates
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cybersecurity HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Information Security Management System ISMS as per the ISO27001 along its complementary Cybersecurity Management and the Privacy Information Management Systems ISO270032, and ISO27701
National Institute of Standards and Technology NIST: Cybersecurity Framework
Payment Card Industry Data Security Standard PCI-DSS
SWIFT Customer Security Programme CSP
SWIFT Customer Security Controls Framework CSCF
Business Continuity Management System BCMS as per the ISO 22301
Cryptika Cybersecurity Company HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Information Security Management System ISMS as per the ISO27001 along its complementary Cybersecurity
Management and the Privacy Information Management Systems ISO270032, and ISO27701
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
National Institute of Standards and Technology NIST: Cybersecurity Framework
Payment Card Industry Data Security Standard PCI-DSS
SWIFT Customer Security Programme CSP
SWIFT Customer Security Controls Framework CSCF
Business Continuity Management System BCMS as per the ISO 22301
Cryptika Cybersecurity Vendor HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Information Security Management System ISMS as per the ISO27001 along its complementary Cybersecurity Management and the Privacy Information Management Systems ISO270032, and ISO27701
National Institute of Standards and Technology NIST: Cybersecurity Framework
Payment Card Industry Data Security Standard PCI-DSS
SWIFT Customer Security Programme CSP
SWIFT Customer Security Controls Framework CSCF
Business Continuity Management System BCMS as per the ISO 22301
Cryptika Cybersecurity Provider HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Information Security Management System ISMS as per the ISO27001 along its complementary Cybersecurity Management and the Privacy Information Management Systems ISO270032, and ISO27701
National Institute of Standards and Technology NIST: Cybersecurity Framework
Payment Card Industry Data Security Standard PCI-DSS
SWIFT Customer Security Programme CSP
SWIFT Customer Security Controls Framework CSCF
Business Continuity Management System BCMS as per the ISO 22301
Cryptika Cybersecurity Firm HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Information Security Management System ISMS as per the ISO27001 along its complementary Cybersecurity Management and the Privacy Information Management Systems ISO270032, and ISO27701
National Institute of Standards and Technology NIST: Cybersecurity Framework
Payment Card Industry Data Security Standard PCI-DSS
SWIFT Customer Security Programme CSP
SWIFT Customer Security Controls Framework CSCF
Business Continuity Management System BCMS as per the ISO 22301
Cryptika Cybersecurity Team HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Information Security Management System (ISMS) as per the ISO 27001 along its complementary Cybersecurity Management and the Privacy Information Management Systems ISO270032, and ISO27701
ISMS Assessment/gap analysis
Organization Context Development
Risk Assessment/Treatment
Staff Training, and Awareness
Engaging ISO PDCA cycle
Forms and Tools Provision
Policies and Procedures (SOPs) Development (ISMS Implementation)
Internal Audit Outsourcing / Co-sourcing
External Audit (Certification Audit) Preparations
penetration testing companies in saudi arabia penetration testing in riyadh penetration testing companies in riyadh penetration testing vendors in middle east penetration testing company in dubai cyber security companies in gulf region cyber security company in dubai in uae service provider in dubai in riyadh in uae in ksa in kuwait
Certification Maintenance
Cryptika Cybersecurity Partner HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Security Operations Centers (SOC) Maturity Assessment
Security Architecture Review
High Level Design (HLD) Review
Configuration Review
Static Application Security Test (SAST) also referred to as "Static Code Security Analysis"
Cryptika Cybersecurity Companies HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Security Operations Centers SOC Maturity Assessment
Security Architecture Review
High Level Design HLD Review
Configuration Review
Static Application Security Test SAST also referred to as "Static Code Security Analysis"
Cryptika Cybersecurity Vendors HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Security Operations Centers SOC Maturity Assessment
Security Architecture Review
High Level Design HLD Review
Configuration Review
Static Application Security Test SAST also referred to as "Static Code Security Analysis"
Cryptika Cybersecurity Providers HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Vulnerabilities Assessments and Penetration Testing (VAPT)
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing (APT)
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test (DAST) as per the OWASP Application Security Verification Standard (ASVS)
Cryptika Cybersecurity Firms HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Cybersecurity Teams HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Cybersecurity Partners HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Dubai, UAE, United Arab Emirates
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Riyadh, KSA, Saudi Arabia
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Information Security HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Information Security Management Systems HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika Information Security Company HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan SWIFT CSP CSCF
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Information Security Vendor HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Information Security Provider HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Information Security Firm HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Cryptika Information Security Partner HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Digital Forensics and Incident Response DFIR
Advanced Email Protection Cloud Delivered Anti-Spam as a Service
Extended EndPoint Detection and Response CrowdStrike
Network Detection and Response NDR
Network Access Control NAC
Privilege Access Management PAM
Active Directory Security Services
Hardware Firewall Solutions Sophos
Cryptika Information Security Companies HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Backup Policies and Procedure SOPs Development
Backup Plan, Implementation, Test and Maintenance
Hardware Provision, Delivery, and on-site installation HPE
Software Installation and Backup Plans Implementation VEEAM
Software Maintenance and Regular Backup Restore Tests
Disaster Readiness Policies and Procedures SOPs Development
Disaster Recovery Site Implementation
DR Site as a Service
DR Continuous Replication Software Installation, and setup
Regular Disaster Recovery Test
Disaster Recovery Policies and Procedures SOPs Development
Enterprise Business Application Migration Services
Mission Critical Migrations Double-Take
Virtualization all platforms including hyper-converged solutions
Hypervisor Migrations
Cloud Migrations
High Availability Solutions
Hyper-Converged Solutions Nutanix, StarWind
Software Defined Datacenters Cryptika Private Cloud
High Availability Fail-Over Clusters Implementation
All kinds of roles Databases, Email, Hypervisors, etc
Load balancing Solutions
Software Defined Load Balncer
Hardware Load Balancing Solutions
Cryptika Information Security Vendors HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Dubai, UAE, United Arab Emirates
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Riyadh, KSA, Saudi Arabia
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Information Security Providers HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Cryptika Information Security Firms HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Backup Policies and Procedure SOPs Development
Backup Plan, Implementation, Test and Maintenance
Hardware Provision, Delivery, and on-site installation HPE
Software Installation and Backup Plans Implementation VEEAM
Software Maintenance and Regular Backup Restore Tests
Disaster Readiness Policies and Procedures SOPs Development
Disaster Recovery Site Implementation
DR Site as a Service
DR Continuous Replication Software Installation, and setup
Regular Disaster Recovery Test
Disaster Recovery Policies and Procedures SOPs Development
Enterprise Business Application Migration Services
Mission Critical Migrations Double-Take
Virtualization all platforms including hyper-converged solutions
SWIFT CSP Provider
swift csp provider
swift csp assessor
swift csp assessment firms
swift csp assessment companies
swift csp assessment vendor
SOC maturity test
soc testing
SOC maturity testing
GRC Consultant
Consulting Firm
Cryptika is a GRC Consulting Firm
providers companies
VAPT Dubai
VAPT UAE
VAPT Amman
VAPT Jordan
VAPT Riyadh
VAPT KSA
VAPT Saudi
Hypervisor Migrations
Cloud Migrations
High Availability Solutions
Hyper-Converged Solutions Nutanix, StarWind
Software Defined Datacenters Cryptika Private Cloud
High Availability Fail-Over Clusters Implementation
All kinds of roles Databases, Email, Hypervisors, etc
Load balancing Solutions
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
SWIFT CSP Provider
swift csp provider
swift csp assessor
swift csp assessment firms
swift csp assessment companies
swift csp assessment vendor
SOC maturity test
soc testing
SOC maturity testing
GRC Consultant
Consulting Firm
Cryptika is a GRC Consulting Firm
providers companies
VAPT Dubai
VAPT UAE
VAPT Amman
VAPT Jordan
VAPT Riyadh
VAPT KSA
VAPT Saudi
Software Defined Load Balncer
Hardware Load Balancing Solutions
Cryptika Information Security Partners HQ Dubai, UAE, United Arab Emirates, Riyadh, KSA, Saudi, Amman, Jordan
Top cybersecurity companies in middle east Cryptika cybersecurity
Top cybersecurity Company in middle east Cryptika cybersecurity
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Top 5 cybersecurity companies in middle east Cryptika cybersecurity
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Top 10 cybersecurity companies in middle east Cryptika cybersecurity
Top cybersecurity companies in Dubai Cryptika cybersecurity
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Top cybersecurity Company in Dubai Cryptika cybersecurity
Top 5 cybersecurity companies in Dubai Cryptika cybersecurity
Top 10 cybersecurity companies in Dubai Cryptika cybersecurity
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Digital Forensics and Incident Response DFIR
Advanced Email Protection Cloud Delivered Anti-Spam as a Service
Extended EndPoint Detection and Response CrowdStrike
Network Detection and Response NDR
Network Access Control NAC
Privilege Access Management PAM
Active Directory Security Services
Hardware Firewall Solutions Sophos
Top cybersecurity companies in Abu Dhabi Cryptika cybersecurity
Top cybersecurity Company in Abu Dhabi Cryptika cybersecurity
Top 5 cybersecurity companies in Abu Dhabi Cryptika cybersecurity
Top 10 cybersecurity companies in Abu Dhabi Cryptika cybersecurity
Top cybersecurity companies in UAE Cryptika cybersecurity
Digital Forensics and Incident Response DFIR
Advanced Email Protection Cloud Delivered Anti-Spam as a Service
Extended EndPoint Detection and Response CrowdStrike
Network Detection and Response NDR
SWIFT CSP Provider
swift csp provider
swift csp assessor
swift csp assessment firms
swift csp assessment companies
swift csp assessment vendor
SOC maturity test
soc testing
SOC maturity testing
GRC Consultant
Consulting Firm
Cryptika is a GRC Consulting Firm
providers companies
VAPT Dubai
VAPT UAE
VAPT Amman
VAPT Jordan
VAPT Riyadh
VAPT KSA
VAPT Saudi
Network Access Control NAC
Privilege Access Management PAM
Active Directory Security Services
Hardware Firewall Solutions Sophos
Top cybersecurity Company in UAE Cryptika cybersecurity
Top 5 cybersecurity companies in UAE Cryptika cybersecurity
Top 10 cybersecurity companies in UAE Cryptika cybersecurity
Backup Policies and Procedure SOPs Development
Backup Plan, Implementation, Test and Maintenance
Hardware Provision, Delivery, and on-site installation HPE
Software Installation and Backup Plans Implementation VEEAM
Software Maintenance and Regular Backup Restore Tests
Disaster Readiness Policies and Procedures SOPs Development
Disaster Recovery Site Implementation
DR Site as a Service
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
DR Continuous Replication Software Installation, and setup
Regular Disaster Recovery Test
Disaster Recovery Policies and Procedures SOPs Development
Enterprise Business Application Migration Services
Mission Critical Migrations Double-Take
Virtualization all platforms including hyper-converged solutions
Hypervisor Migrations
Cloud Migrations
High Availability Solutions
Hyper-Converged Solutions Nutanix, StarWind
Software Defined Datacenters Cryptika Private Cloud
High Availability Fail-Over Clusters Implementation
All kinds of roles Databases, Email, Hypervisors, etc
Load balancing Solutions
Software Defined Load Balncer
Hardware Load Balancing Solutions
Top cybersecurity companies in KSA Cryptika cybersecurity
Top cybersecurity Company in KSA Cryptika cybersecurity
Top 5 cybersecurity companies in KSA Cryptika cybersecurity
Top 10 cybersecurity companies in KSA Cryptika cybersecurity
Top cybersecurity companies in Riyadh Cryptika cybersecurity
Backup Policies and Procedure SOPs Development
Backup Plan, Implementation, Test and Maintenance
Hardware Provision, Delivery, and on-site installation HPE
Software Installation and Backup Plans Implementation VEEAM
Software Maintenance and Regular Backup Restore Tests
Disaster Readiness Policies and Procedures SOPs Development
Disaster Recovery Site Implementation
DR Site as a Service
DR Continuous Replication Software Installation, and setup
Regular Disaster Recovery Test
Disaster Recovery Policies and Procedures SOPs Development
Enterprise Business Application Migration Services
Mission Critical Migrations Double-Take
Virtualization all platforms including hyper-converged solutions
Hypervisor Migrations
Cloud Migrations
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
High Availability Solutions
Hyper-Converged Solutions Nutanix, StarWind
Software Defined Datacenters Cryptika Private Cloud
High Availability Fail-Over Clusters Implementation
All kinds of roles Databases, Email, Hypervisors, etc
Load balancing Solutions
Software Defined Load Balncer
Hardware Load Balancing Solutions
Top cybersecurity Company in Riyadh Cryptika cybersecurity
Top 5 cybersecurity companies in Riyadh Cryptika cybersecurity
Digital Forensics and Incident Response DFIR
Advanced Email Protection Cloud Delivered Anti-Spam as a Service
Extended EndPoint Detection and Response CrowdStrike
Network Detection and Response NDR
Network Access Control NAC
Privilege Access Management PAM
Active Directory Security Services
Hardware Firewall Solutions Sophos
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Top 10 cybersecurity companies in Riyadh Cryptika cybersecurity
Top cybersecurity companies in Kuwait Cryptika cybersecurity
Top cybersecurity Company in Kuwait Cryptika cybersecurity
Top 5 cybersecurity companies in Kuwait Cryptika cybersecurity
Top 10 cybersecurity companies in Kuwait Cryptika cybersecurity
Top cybersecurity companies in Amman Cryptika cybersecurity
Backup Policies and Procedure SOPs Development
Backup Plan, Implementation, Test and Maintenance
Hardware Provision, Delivery, and on-site installation HPE
Software Installation and Backup Plans Implementation VEEAM
Software Maintenance and Regular Backup Restore Tests
SWIFT CSP Provider
swift csp provider
swift csp assessor
swift csp assessment firms
swift csp assessment companies
swift csp assessment vendor
SOC maturity test
soc testing
SOC maturity testing
GRC Consultant
Consulting Firm
Cryptika is a GRC Consulting Firm
providers companies
VAPT Dubai
VAPT UAE
VAPT Amman
VAPT Jordan
VAPT Riyadh
VAPT KSA
VAPT Saudi
Disaster Readiness Policies and Procedures SOPs Development
Disaster Recovery Site Implementation
DR Site as a Service
DR Continuous Replication Software Installation, and setup
Regular Disaster Recovery Test
Disaster Recovery Policies and Procedures SOPs Development
Enterprise Business Application Migration Services
Mission Critical Migrations Double-Take
Virtualization all platforms including hyper-converged solutions
Hypervisor Migrations
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Cloud Migrations
High Availability Solutions
Hyper-Converged Solutions Nutanix, StarWind
Software Defined Datacenters Cryptika Private Cloud
High Availability Fail-Over Clusters Implementation
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
All kinds of roles Databases, Email, Hypervisors, etc
Load balancing Solutions
Software Defined Load Balncer
Hardware Load Balancing Solutions
Top cybersecurity Company in Amman Cryptika cybersecurity
Top 5 cybersecurity companies in Amman Cryptika cybersecurity
Digital Forensics and Incident Response DFIR
Advanced Email Protection Cloud Delivered Anti-Spam as a Service
Extended EndPoint Detection and Response CrowdStrike
Network Detection and Response NDR
Network Access Control NAC
Privilege Access Management PAM
Active Directory Security Services
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Hardware Firewall Solutions Sophos
Top 10 cybersecurity companies in Amman Cryptika cybersecurity
Top cybersecurity companies in Jordan Cryptika cybersecurity
Top cybersecurity Company in Jordan Cryptika cybersecurity
Top 5 cybersecurity companies in Jordan Cryptika cybersecurity
Backup Policies and Procedure SOPs Development
Backup Plan, Implementation, Test and Maintenance
Hardware Provision, Delivery, and on-site installation HPE
Software Installation and Backup Plans Implementation VEEAM
Software Maintenance and Regular Backup Restore Tests
Disaster Readiness Policies and Procedures SOPs Development
Disaster Recovery Site Implementation
DR Site as a Service
DR Continuous Replication Software Installation, and setup
Regular Disaster Recovery Test
Disaster Recovery Policies and Procedures SOPs Development
Enterprise Business Application Migration Services
Mission Critical Migrations Double-Take
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Virtualization all platforms including hyper-converged solutions
Hypervisor Migrations
Cloud Migrations
High Availability Solutions
Hyper-Converged Solutions Nutanix, StarWind
Software Defined Datacenters Cryptika Private Cloud
High Availability Fail-Over Clusters Implementation
All kinds of roles Databases, Email, Hypervisors, etc
Load balancing Solutions
Software Defined Load Balncer
Hardware Load Balancing Solutions
Top 10 cybersecurity companies in Jordan Cryptika cybersecurity
Cryptika Cryptica Based in Amman in Jordan Cryptika is a cyber security and IT security service provider providers company companies and a vendor vendors of antivirus Cryptic provider Cryptik penetration testing penetration testers tester test penetration pentest pentesting hacking ethical hackers ethical hacker hacking SOC Managed SOC Consulting Consultants consultant Information security IT Security IT Governance Risk management best practices GRC SIEM SOAPA Information security assurance cybersecurity assurance it assurance security assurance availability assurance business continuity assurance digital forensics DFIR Security Architecture Review Architect HLD High Level Design Review Configuration Review Config Security Configuration change management compliance and audit data leakage prevention Cyber Security Next-Generation penetration testers testing test penetration Antivirus Digital Forensics and Incident Response DFIR
Advanced Email Protection Cloud Delivered Anti-Spam as a Service
Extended EndPoint Detection and Response CrowdStrike
Network Detection and Response NDR
Network Access Control NAC
Privilege Access Management PAM
Active Directory Security Services
Hardware Firewall Solutions Sophos
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
information security jordan
Vulnerabilities Assessments and Penetration Testing VAPT
Business Applications Penetration Testing
Network Penetration Testing
Mobile Application Penetration Testing
Advanced Penetration Testing APT
Red-Teaming Engagements
Phishing and Vishing Testing
DDoS Stress Testing
Dynamic Application Security Test DAST as per the OWASP Application Security Verification Standard ASVS
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Dubai, UAE, United Arab Emirates
SWIFT CSP CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
Cryptika Cyber security Firms Riyadh, KSA, Saudi Arabia
SWIFT CSP Provider Assessor CSCF NIST GDPR HIPAA PCI-DSS ISMS BCMS NCA ECC CITC CRF SAMA CSF NESA SIA ISR CBJ Saudi Arabia’s National Cybersecurity Authority NCA: Essential Cybersecurity Controls ECC
Saudi Arabia's Communication and Information Technology Commission CITC: Cybersecurity Regulatory Framework CRF
Saudi Arabian Monetary Authority SAMA: Cyber Security Framework CSF
UAE National Electronic Security Authority NESA: Information Assurance Standard SIA
Dubai Electronic Security Center: Information Security Regulation v2 ISR
Central Bank of Jordan CBJ: Cyber Security Framework CSF
it security services jordan
dast, sast, code review, dynamic application security testing, static application security testing, static code analysis, PT, dast, sast, vapt, va,
it security jordan cyber security jordan pentester penetration testers jordan
penetration tester jordan tester
DAST SAST Jordan SAST service in jordan SAST jordan DAST Jordan SAST Professional
Netsparker Jordan Netsparker partners in middle east fortify acunetix
test testing assess infrastcuture
ddos OWASP TOP 10 VAPT Jordan VAPT VA PT VAPT services VAPT service VAPT Professional VAPT in Jordan VAPT Amman OWASP TOP 10 VAPT in Amman
dos attack zero day zeroday SWIFT CSP CSCF zero-day 0day vulnerabilities vulnerability assessment management IT Security center forum comession department Cryptika SOC Cb Defense is certified to replace antivirus Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
meet PCI and HIPAA ISO 27001 COBIT ITIL compliance requirements and protect information in the cloud. PCI-DSS Certificate lead implementer auditor That's why Cb Defense is trusted by leading analysts and industry associations Cryptica Crypto Cyber Intelligence cyber detective Cybereason antiransomware ransomware protection zero-day attacks protection Cb Response Protection Cb Defense is proven to replace AV with better protection increased visibility and an easy experience that keeps users productive. Backed by world-class threat research and customer service our customers know their security comes first. UEBA UBEA Beyond the Hype: AI Machine Learning & Non-Malware Attacks. Detect attacks in progress and respond immediately. Cryptika offers endpoint detection and blocking granularity like never before! We were able to detect and block bitcoin mining software that wasn't even detected. Security as a service MSSP in jordan, MSSPs Jordan, MSP Jordan, dast, sast, code review, dynamic application security testing, static application security testing, static code analysis, PT, dast, sast, vapt, va, MSP in Jordan, MSSP companies in Jordan, MSPs Managed security services providers companies in Jordan MSSP Security as a service information security Red team red teaming black hackers black hat gray hat white box black box audit auditors auditor IT auditing audit companies in Jordan IT audit security vendors providers firms firm vendor provider audit information security audit external internal audit Managed Services EDR vendors in Jordan in middle east NGAV vendors in Jordan DAST SAST Jordan SAST service in jordan SAST jordan DAST Jordan SAST Professional
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Netsparker Jordan Netsparker partners in middle east fortify acunetix NGAV vendor Broadest Security Coverage Indecent Response for SOC Teams one of the Top IT Security Companies in Jordan and Middle East best Antivirus 2017 -2018 Best IT Security companies company Anti-Spam vendor Carbon Black Partner Cylance crowdstrike crowd strike Carbon Black Partners in jordan Carbon Black Partners in middle east Partner Kaspersky vs trendmicro trend micro vs Kaspersky vs Symantec vs Norton vs Cryptika vs Kaspersky vs sophos vs sofos vs cyberoam vs Kaspersky vs Carbon Black vs McAfee vs Kaspersky vs MalwareBytes vs fortinet vs Palo Alto vs IBM Security vs Splunk vs QRadar vs AlienVault Top Antivirus threat intelligence vendors Carbon Black Distributor Disti our office in Amman NSS SWIFT CSP CSCF report 100% AEP Gartner ATP Advanced Threat Prevention Sandbox
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
LastLine Antivirus Vendor top Antivirus Companies Solve Ransomware Restore data encrypted data Stop Ransomware fabric solutions WannaCry EDR NGAV Companies EDR dast, sast, code review, dynamic application security testing, static application security testing, static code analysis, PT, dast, sast, vapt, va, Fortify partners in jordan veracode partners jordan acunetix partners in jordan netsparker partners in jordan cloudflare partners in jordan ssl certificate wildcard pentesting using cobaltstrike 4.0 in jordan metaspolit rapid7 mimikatz domain attacks, DCShadow DCSync NTLM protection SandBoxing Threat Hunting Vendor Threat Hunting Vendors in Jordan Clean Virus Ransomware EDR Endpoint detection response IR Product Cyber Threats Hunter Firewall Encryption Protect against Ransomware Protect your organization against zero-day attacks Script based Attacks fileless attacks Powershell attacks behavior Cryptika correlation Threat Intelligence Prevent Malware and non-Malware non Malware and non-file based attack non file based attack non malware based attack detect unusual activity suspicious activity anomaly anomalies Sandboxing sandbox NG AV NG AV Vendor dast, sast, code review, dynamic application security testing, static application security testing, SWIFT CSP CSCF static code analysis, PT, dast, sast, vapt, va What is NGAV What is Next-Generation Antivirus Cool Vendor Gartner Magic Quadrant Named Leader EDR EMEA Vendor Partner Partners Vendors Middle East Vendor NGAV EDR Reseller re-sellers Resellers Jordan Consulting Consultant Outsourcing Infosec VEEAM partner partners in jordan ibm Microsoft exchange Microsoft Azure 365 dynamics best security company companies company in Amman emea middle east Saudi Arabia UAE Information Security MSSP MSP Managed security services provider (NGAV) (EDR) Next-Generation Endpoint Security Next Generation NGAV AV Cryptika Antivirus Anti-Virus Legacy AV Zero-Day Attack Attacks Malicious Activities OWASP TOP 10 VAPT Jordan VAPT VA PT VAPT services VAPT service VAPT Professional VAPT in Jordan VAPT Amman VAPT Cryptika Machine Learning Engine Recognizes Behaviors Lateral Movement Visualize Remediation with Precision Demo Trial Data Breach Sandbox Sandboxing Fortinet Lastline Cloud-Delivered Next-Gen Managed Threat Hunting Proactive Falcon Platform Lightweight PREVENTION Cryptika SWIFT CSP CSCF Gartner Magic Quadrant Cryptika Named Leader Vendor NSS report NGAV EDR Incident Response Platform Market Leading Application Control Cb Defence Real-Time Recording Stop Malware PCI DSS COBIT ITIL ISO HIPAA SANS AI Carbon Black Partners in Jordan IT Governance IT Compliance Management Standardization IT Risk Assessments Risk Management SLA isaca BSI pci-dss process analysis consulting methodology soc development deployment vulnerability assessment management business impact analysis web application penetration testing security scan scanning CISSP CISP CISA CISM lead implementer IEC CIHE Certified penetration tester testers accreditation DAST SAST Jordan SAST service in jordan SAST jordan DAST Jordan SAST Professional
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Netsparker Jordan Netsparker partners in middle east fortify acunetix information security manager management GDPR Indecent response handling lead implementer auditor Streaming Prevention Our Company's address is in Amman red team redteam threat hunter responder SOC analyst CyberSec 22001 ISO 2000289 VAPT Jordan VAPT VA PT VAPT services OWASP TOP 10 VAPT service VAPT Professional VAPT in Jordan VAPT Amman VAPT Jordan Endpoint Detection and Response Threat Intelligence Crypto Threat Hunting Cryptika NGAV Company in Jordan Digital Forensics non-Malware non-file based attack Cyber Security Companies in Jordan in Amman IT SWIFT CSP CSCF Security Company in Jordan Amman Cryptika Jordan based Digital Transformation Technology SOC Security Operation Center AlienVault Qradar ArcSight Splunk QRadar FireEye IT Audit ISO27001 Qualys Rabid7 Metasploit Vulnerability Management Assessment Information Security Companies in Jordan IT Company Backup HA Cb Defense Vendors in Jordan Cb Defense Re-sellers in Jordan We protect your Organization with Carbon Black Cb Defense Cb Response SecureTide Cryptika Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Cryptika High Availability Solutions Double-Take MIMEX VEEAM HyperV Wakalat St. Next-generation antivirus + EDR in one cloud-delivered platform that stops malware non-malware attacks and non-file attacks Anti Ransomware Protect Against WannaCry Carbon Black Crowdstrike Cybereason Enterprise protection Kaspersky Symantec Threat hunt detect correlation Malware non-Malware non-file based attack Powershell script EMEA Adversary hunting Hunt automation EDR Endpoint Response bug bounty ctf soc2 soc3 top IT Security company in Jordan best it security company in Jordan Antivirus companies in Jordan Antivirus vendors in Jordan Product: Antivirus Next-Generation Antivirus Endpoint Detection and Response Best IT Security Company in Jordan Stop WannaCry Top IT Security Company in Jordan
Advanced Penetration Testing Services Advanced Attack Simulation Application Security Assessment Kali Linux wireless attacks OSCP OSWP OSCE OSEE OSWE KLCP comprehensive cisco qualys tenable nessus CEH big assessment gap analysis risk impact statement applicability Open threat exchange sqrl exploitation expert live ops sla service level agreement protocol NSA CIA Cryptika is a partner of Carbon Black qualified code review secure coding firewall firewalls fortinet fortigate paloalto veeam emea partners in jordan in saudi arabia ryadh jedda uae dubai irbid advanced malware protection lastline privileged acros sailpoint enterprise data governance varonis netwrix log and event management security information and event management system social engineering becb ec-council linux foundation linux redhat fedora mandriva infrastructure security assessment Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
debian identity management Partners in Jordan EDR Endpoint Detection and Response Security Firm EMEA Security Vendors Carbon Black EMEA Partners Carbon Black Middle East Partners Qualys Partners soc managed in amman Petya / NotPetya Ransomware zeroday zero day attacks Advanced threat protection IT Security Companies in Jordan Address: AlSwifieh Amman Jordan
[email protected] Streaming Prevention Carbon Black partners IT Company in Jordan Safwan Talab digitization digital transformation xacker consulting IT firm IT Consulting Audit iso27001 COBIT Business companies in Jordan providers in Jordan vendors in Jordan distributors in Jordan dealers in Jordan Continuity
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Middle East vendors companies providers firms mssp DAST SAST Jordan SAST service in jordan SAST jordan DAST Jordan SAST Professional
Netsparker Jordan Netsparker partners in middle east fortify acunetix
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
twitter.com/cryptika
@cryptika
VAPT Jordan VAPT VA PT VAPT services VAPT service VAPT Professional VAPT in Jordan VAPT Amman VAPT
linkedin.com/company/cryptika
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
pentester
pentesting
pentesters
CTF jordan
Bug Bounty jordan
Catch the flag
hacker box
hackbox
OSCP
OSCE
soapa
SOAR
TIPs
TIP
SOAPA
Cryptika COMPANY AMMAN JORDAN Cryptika is primarily recognized as information security firm delivering end to end comprehensive security offensive security
Cryptika is the first and only Information security center and a firm and a company in Jordan amman which dedicated all its experine in cyber security and cybersecurity
Security Solutions, Security Consultancy, Cyber Security, Cybersecurity, Information Security, NETWORKS AND INFORMATION SECURITY ENGINEERING, Security Services such Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
penetration testing and vulnerability assessment, Vulnerability Assesment and Penetration Testing (VAPT) Service. This service enable to find vulnerabilities in network devices, application and using security, Jordan National Cyber Security Strategy
headquarters in Jordan, Cryptika operates in amman jordan
Cryptika is a Jordanian IT security company Specialized in information and Cyber Security, and information security. Cryptika is r in jordan and middle east, HQ based in Amman
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Cyber Security & Forensic Services in an event where you can gain a comprehensive insight into the agenda of the most important institutions and companies such as Cryptika
The terms information security, computer security and information assurance are on top of our services
IT penetration testing ... Internal and external penetration tests and IT security analysis can provide those ... ...
Cryptika CyberSecurity, Cyber Security, Information Security, IT Security, Penetration Testing, Vulnerability Assessment, IT Security Assessment, Security Assessment, Threat Hunting, Red Teaming,
cryptika is a Jordanian Company Speciallized in Cybersecurity
digital transformation in jordan
digital transformation companies jordan
digital transformation technology
الفريق العربي للبرمجة
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
JAASCIOS
JAASCOIS
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
JAAS
arabteam2000
fintec Jordan central bank social engineering services phishing testing vishing testing service phishing testers in jordan amman security solutions network security engineer career position information security officer analyst analysis soc engineer level two three one 1 2 3 level sla service level agreement manager officer job
OWASP TOP 10 VAPT Jordan VAPT VA PT VAPT services VAPT service VAPT Professional VAPT in Jordan VAPT Amman VAPT
Web Browsers
Burp Suite Professional
NetSparker Enterprise
Acunetix
SoapUI
Traceable AI
Postman HTTP Client
Taurus
Custom Perl Scripts
Activities summary: The following activities is a quick summary of what will be performed during the pentest:
Obtain all needed information about the target applications.
Agree with on the actions that will be taken if critical vulnerabilities discovered during the assessment.
Agree with IT systems owners on the assessment schedules and plans.
Conduct thorough information security vulnerability scanning for the servers that host and run web applications; to explore all security vulnerabilities and gaps on the server’s operating systems and network configurations. Because any security gap in the hosted server is considered a security gap for the web application; the server’s vulnerability can be exploited to attack any running application on that server.
Assess web applications against the ten most critical web application security risks announced by OWASP. OWASP Top 10 2021 (latest release) and the older version of 2017:
A01:2021-Broken Access Control
A02:2021-Cryptographic Failures
A03:2021-Injection
A04:2021-Insecure Design
A05:2021-Security Misconfiguration
A06:2021-Vulnerable and Outdated Components
A07:2021-Identification and Authentication Failures
A08:2021-Software and Data Integrity Failures
A09:2021-Security Logging and Monitoring Failures
A10:2021-Server-Side Request Forgery
A1:2017-Injection
A2:2017-Broken Authentication
A3:2017-Sensitive Data Exposure
A4:2017-XML External Entities (XXE)
A5:2017-Broken Access Control
A6:2017-Security Misconfiguration
A7:2017-Cross-Site Scripting (XSS)
A8:2017-Insecure Deserialization
A9:2017-Using Components with Known Vulnerabilities
A10:2017-Insufficient Logging & Monitoring
All gathered information will be then thoroughly analyzed to know how attackers can take advantages of these vulnerabilities.
Exploitation Attempt: Once exploitable vulnerabilities are identified, hacking scenarios will be developed and PT team will coordinate with regarding schedule/ methods of applying these scenarios on the production environment; taking into consideration the effect on business operation. After that, the actual penetration is carried out and evidence of penetration (such as a screen shot) is collected. Possible Scenarios Include:
Account Brute force/ Dictionary Attacks
Known Vulnerability Exploitation
Taking the advantage of misconfiguration, Input Fields or transaction flow.
Backdoor/ Trojan Installation.
Sensitive Data Acquisition.
Cookie Hijacking.
Directory Traversal.
Cleaning Up: Once penetration is completed and documented, any changes made to the targeted system will be reversed.
Automated Vulnerabilities Scans
Before starting our penetration testing activities, Cryptika lunch a number of automated scans to ensure full testing coverage, our team will develop a full proxy record of every page request, and a full proxy record of every subsequent request that was generated as a result of exercising the application. All of the java script, style sheet, web service and image requests that would have been nearly impossible to list have been captured. Our team will also made rational, informed human decisions about what not to do, like continuing to pursue dynamic URLs forever. That resource list now becomes the scanner target list. After checking to ensure that the scanner is configured as prescribed in our scope documents, including any scope or safety clarifications we may have received, cryptika launch automated scans. After automated scans have completed, which may require adjustments for IPS or WAF evasion, we will have a scanner report. Cryptika look very closely at the vulnerability scan results. We take note of any identified vulnerabilities and start sorting them into two buckets - those that require further validation and those that are reliable and need no further validation. We are not just looking for vulnerabilities that the scanner identified though. We look at vulnerability scans differently than most. For us, the results are a record of tens or hundreds of thousands of interactions with your application, and we look for anything in those results that seems out of the ordinary at all. It is surprising how often you can find hints that lead you to really serious vulnerabilities when you combine knowledgeable, informed human intuition with scanner output. We look hard.
Filtering Vulnerabilities Scan Results
After the automated scans and filtering its false-positives, we look at everything that has been identified for further testing. This is the point at which it is impossible to list tools or methods because there is simply too much potential ground to cover, but very often we will use Burp Suite Intruder and/or Repeater. In general, vulnerabilities will fall into three categories at this point:
Vulnerabilities that were identified by automation and are reliable. A finding report is prepared, along with any validating evidence from the automated tool.
Vulnerabilities that were identified by automation but are not reliable until validated. These are validated using whatever tools or methods are appropriate. Screen captures and other evidence is collected and a finding report is created.
Possible vulnerabilities or simple suspicions identified manually. These are all tested, one way or another, until we are convinced that we know what we are seeing, and can either dismiss them or report them.
Manual Application Crawling/Review
Full Exercise with Proxy Capture
The first thing our team do here is to set up the testing browser to use a proxy tool that captures every web request. From that point on the team will fully exercise the application, while taking notes about what they see. The main purpose here is to exercise the application fully, capture all of the traffic, gain a full understanding of the application, and take notes.
Scope Checks
One of the things our team look for in this phase is any indication of scope problems that require clarification, such as mixed protocol schemes (https is in scope, but http is not mentioned and we find both), or the application is making requests to different host specifiers than expected, and we need to know if your intent was different than what actually ended up in our scope documents. Cryptika try to ensure that scope is accurate before we even begin, but it is important for testers to be very 'scope aware' and to identify any such issues as early as possible and get clarification.
Safety and Stability Checks
Our testers are taking notes about many things, but none are more important than identifying potential safety and stability factors. Any login forms, email forms, database forms, or other potential problem areas are identified. Again, we try to identify and address problem areas in our scope documents before testing even begins, but our testers are trained to look for anything that might have been missed in planning.
Side Channel Vulnerabilities
While exercising the application, Cryptika look at any email, text messaging or other out of band communication sent to us by the web application. This is something that scanners can't do very well, and we look closely at everything the application does.
Logical Faults
There may be some issues that can be fully documented into finding reports immediately, without performing any testing that would raise flags with an application firewall or IPS, and if so, we do it. This often involves so called 'logical faults', and we find them often in login pages, password reset pages, and account registration pages. For findings that require further intrusive testing, we just take notes for later follow up.
Application Penetration Testing
Each task below will include a similar diagram depicting the process flow.
Application Mapping. This series tasks of penetration testing focuses on the gathering of information and allows the testers to gain a firm understanding of the user interface or web service functionality and design. Where it almost 90% dependent on outputs
Application Platform Fingerprinting
Task Description: Use tools to query the application service to identify the platform type and version hosting the application. (Such as Apache and Tomcat)
Identify the application server and technologies used to host the application.
Functional Analysis
Gain an understanding of the application from the user’s perspective. Explore the application and identify major functionality and features exposed to the user. Identify major sections and portions of the application, including the user roles.
Gain a better understanding of the application for later analysis.
Process Flow Modeling
Identify dependencies between actions and requirements to get to each portion of the application.
Gain a better understanding of the application for later analysis.
Request/Resource Mapping
Attempt to map, execute, and record every possible request in the application. Examine the requests and responses to understand how the application works from the developer’s perspective. Identify parameter names and values that are reflected back to the user or appear to be used in a database query.
Identify requests that have a higher probability of containing vulnerabilities. Prioritize for later analysis.
Application Discovery. penetration testing focuses on the identification of vulnerabilities in the user interfaces or web services.
Configuration Management Testing
Test the platform and application server configuration, such as SSL/TLS testing, file extension handling, method handling, and the existence of administrative interface and unreferenced links.
Identify vulnerabilities in the application.
Authentication Testing
Test the application authentication for flaws such as user enumeration, guessable passwords, authentication bypass, flawed password reset, race conditions, multifactor authentication, and CAPTCHA implementation weaknesses.
Identify vulnerabilities in the application.
Session Management Testing
Test the application for session management flaws such as session fixation, session hijacking, unprotected session keys, and Cross Site Request Forgery (CSRF).
Identify vulnerabilities in the application.
Authorization Testing
Test the application for authorization flaws such as path traversal, authorization bypass, and privilege escalation.
Identify vulnerabilities in the application.
Business Logic Testing
Task Description: Test the business logic flow and user process flow to verify steps that cannot be skipped or re-ordered.
Identify vulnerabilities in the application.
Data Validation Testing
Task Description: Test the application for data validation flaws such as XSS, SQL Injection, LDAP injection, XPath Injection, overflows, format string issues, and HTTP Splitting.
Identify vulnerabilities in the application.
Application Exploitation. penetration testing focuses on the exploitation of vulnerabilities found in the previous tasks and the escalation of access the tester has in the application.
Identify Attack Avenues
Review all findings and outputs from previous tasks and identify plausible attacks that have a moderate chance of success. Prioritize these possible attacks by likelihood and the tester’s ability to execute them.
Organize and plan next steps.
Vulnerability Exploitation
Create proof of concept attacks to demonstrate the feasibility and business risk created by the discovered vulnerabilities. Once a vulnerability has been exploited, attempt to pivot and identify additional vulnerabilities to exploit.
Validate the assumed business risks created by the identified vulnerabilities and identify additional targets of opportunity.
Post Exploitation
Remove any code, date, or configurations that were added to the system as a part of the assessment.
Return systems to their pre-assessment state.
Testing checklist (the scenarios)
Security Testing Scenarios
Check for SQL injection attacks
Secure pages should use HTTPS protocol
Page crash should not reveal application or server info. Error page should be displayed for this
Escape special characters in input
Error messages should not reveal any sensitive information
All credentials should be transferred over an encrypted channel
Test password security and password policy enforcement
Check application logout functionality
Check for Brute Force Attacks
Cookie information should be stored in encrypted format only
Check session cookie duration and session termination after timeout or logout
Session tokens should be transmitted over secured channel
Password should not be stored in cookies
Test for Denial-of-Service attacks
Test for memory leakage
Test unauthorized application access by manipulating variable values in browser address bar
Test file extension handing so that exe files are not uploaded and executed on server
Sensitive fields like passwords and credit card information should not have auto
Verify CAPTCHA functionality
Security Testing as Part of API Testing
In software Penetration testing Cryptika will look at the most critical OWASP security problems for APIs and potential test cases to find them.
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika Cyber security Cryptika is a fully integrated cyber security and managed services provider comprise a comprehensive team of experts and thought leaders. Our scope of work includes everything from design, implementation and procurement of high tech IT infrastructure to cyber security, cyber surveillance and full IT managed services
Cryptika Cryptica Based in Amman in Jordan Cryptika is a cyber security and IT security service provider providers company companies and a vendor vendors of antivirus Cryptic provider Cryptik penetration testing penetration UAE testers tester test penetration pentest pentesting hacking ethical hackers ethical hacker hacking SOC Managed SOC Consulting Consultants
consultant Information security Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
IT Security IT Governance Risk management best practices SIEM SOAPA Information security assurance cybersecurity assurance it assurance security assurance availability assurance business continuity assurance digital forensics DFIR change management compliance and audit data leakage prevention Cyber Security Next-Generation penetration testers testing test penetration Antivirus Cybersecurity NGAV Threat Hunting Threat Hunt NG AV Intelligence threat intelligence Security operations center Information security Dubai services in jordan information security jordanit security services jordanit security jordan cyber security jordan
pentester penetration testers jordanpenetration tester jordantestertest testing assess infrastcutureddosdos attack zero day zeroday zero-day 0day vulnerabilities vulnerability assessment management IT Security center forum comession department Cryptika SOC Cb Defense is certified to replace antivirus meet PCI and PCI-DSS ISMS BCMS HIPAA ISO 27001 COBIT ITIL compliance requirements and protect information in the cloud. PCI-DSS Certificate lead implementer auditor That's why Cb Defense is trusted by leading analysts and industry associations Cryptica Crypto Cyber Intelligence cyber detective Cybereason antiransomware ransomware protection zero-day attacks protection Cb Response Protection Cb Defense is proven to replace AV with better protection increased visibility and an easy experience that keeps users productive. Backed by world-class threat research and customer service our customers know their security comes first. UEBA UBEA Beyond the Hype: AI Machine Learning & Non-Malware Attacks. Detect attacks in progress and respond immediately. Cryptika offers endpoint detection and blocking granularity like never before! We were able to detect and block bitcoin mining software that wasn't even detected. Security as a service MSSP in jordan, MSSPs Jordan, MSP Jordan, MSP in Jordan, MSSP companies in Jordan, MSPs Managed security services providers companies in Dubai UAE, in Riyadh Saudi KSA in Amman Jordan MSSP Security as a service information security Red team red teaming black hackers black hat gray hat white box black box audit auditors auditor IT auditing audit companies in Jordan IT audit security vendors providers firms firm vendor provider audit information security audit external internal audit Managed Services EDR vendors in Jordan in middle east NGAV vendors in Jordan NGAV vendor Broadest Security Coverage Indecent Response for SOC Teams one of the Top IT Security Companies in Jordan and Middle East best Antivirus 2017 -2018 Best IT Security companies company Anti-Spam vendor Carbon Black Partner Cylance crowdstrike crowd strike Carbon Black Partners in jordan Carbon Black Partners in middle east Partner Kaspersky vs trendmicro trend micro vs Kaspersky vs Symantec vs Norton vs Cryptika vs Kaspersky vs sophos vs sofos vs cyberoam vs Kaspersky vs Carbon Black vs McAfee vs Kaspersky vs MalwareBytes vs fortinet vs Palo Alto vs IBM Security vs Splunk vs QRadar vs AlienVault Top Antivirus threat intelligence vendors Carbon Black Distributor Disti our office in Amman NSS report 100% AEP Gartner ATP Advanced Threat Prevention Sandbox LastLine Antivirus Vendor top Antivirus Companies Solve Ransomware Restore data encrypted data Stop Ransomware fabric solutions WannaCry XDR NDR EDR NGAV Companies EDR Threat Hunting Vendor Threat Hunting Vendors in Jordan Clean Virus Ransomware EDR Endpoint detection response IR Product Cyber Threats Hunter Firewall Encryption Protect against Ransomware Protect your organization against WannaCry and Petya / NotPetya Prevent zero-day attacks Script based Attacks Powershell attacks behavior Cryptika correlation Threat Intelligence Prevent Malware and non-Malware non Malware and non-file based attack non file based attack non malware based attack detect unusual activity suspicious activity anomaly anomalies Sandboxing sandbox NG AV NG AV Vendor What is NGAV What is Next-Generation Antivirus Cool Vendor Gartner Magic Quadrant Named Leader EDR EMEA Vendor Partner Partners Vendors Middle East Vendor NGAV EDR Reseller re-sellers Resellers Jordan Consulting Consultant Outsourcing Infosec VEEAM partner partners in jordan ibm Microsoft exchange Microsoft Azure 365 dynamics best security company companies company in Amman emea middle east Saudi Arabia UAE Information Security MSSP MSP Managed security services provider (NGAV) (EDR) Next-Generation Endpoint Security Next Generation NGAV AV Cryptika Antivirus Anti-Virus Legacy AV Zero-Day Attack Attacks Malicious Activities Cryptika Machine
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Sandbox Sandboxing Fortinet Lastline Cloud-Delivered Next-Gen Managed Threat Hunting Proactive Falcon Platform Cryptika Gartner Magic Quadrant Cryptika Named Leader Vendor NSS report NGAV EDR Incident Response Platform Market Leading Application Control Cb Defence Real-Time Recording Stop Malware PCI DSS COBIT ITIL ISO HIPAA SANS AI Carbon Black Partners in Jordan IT Governance IT Compliance Management Standardization IT Risk Assessments Risk Management SLA isaca BSI pci-dss process analysis consulting methodology soc development deployment vulnerability assessment management business impact analysis web application penetration testing security scan scanning
Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
CISSP CISP CISA CISM OWASP TOP 10 lead implementer IEC CIHE Certified penetration tester testers accreditation information security manager management GDPR Indecent response handling lead implementer auditor Streaming Prevention Our Company's address is in Amman red team redteam threat hunter responder SOC analyst CyberSec 22001 ISO 2000289 Jordan Endpoint Detection and Response Threat Intelligence Crypto Threat Hunting Cryptika NGAV Company in Jordan Digital Forensics non-Malware non-file based attack Cyber Security Companies in Jordan in Amman IT Security Company in Jordan Amman Cryptika Jordan based Digital Transformation Technology SOC Security Operation Center AlienVault Qradar ArcSight Splunk QRadar FireEye IT Audit ISO27001 Qualys Rabid7 Metasploit Vulnerability Management Assessment Information Security Companies in Jordan IT Company Backup HA Cb Defense Vendors in Jordan Cb Defense Re-sellers in Jordan We protect your Organization with Carbon Black Cb Defense Cb Response SecureTide Cryptika High Availability Solutions Double-Take MIMEX VEEAM HyperV Wakalat St. Next-generation antivirus + EDR in one cloud-delivered platform that stops malware non-malware attacks and non-file attacks Anti Ransomware Protect Against WannaCry Carbon Black Crowdstrike Cybereason Enterprise protection Kaspersky Symantec Threat hunt detect correlation Malware non-Malware non-file based attack Powershell script EMEA Adversary hunting Hunt automation EDR Endpoint Response top IT Security company in Jordan best it security company in Jordan Antivirus companies in Jordan Antivirus vendors in Jordan Product: Antivirus Next-Generation Antivirus Endpoint Detection and Response Best IT Security Company in Dubai Riyadh Amman UAE KSA Jordan Stop WannaCry Top IT Security Company in Jordan Advanced Penetration Testing Services Advanced Attack Simulation Application Security Assessment Kali Linux
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
wireless attacks OSCP OSWP OSCE OSEE OSWE KLCP comprehensive cisco qualys tenable nessus CEH big assessment gap analysis risk impact statement applicability Open threat exchange sqrl exploitation expert live ops sla service level agreement protocol NSA CIA Cryptika is a partner of Carbon Black qualified code review secure coding firewall firewalls fortinet fortigate paloalto veeam emea partners in jordan in saudi arabia ryadh jedda uae dubai irbid advanced malware protection lastline privileged acros sailpoint enterprise data governance varonis Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Our Office in Amman, Jordan: Address: Al Ghodaf Center #15 Wakalat Street, Al-Swiefieh, Amman, Jordan 962 6 2000 289
[email protected]
Our Office in Doha, Qatar: Address: Al Fardan Tower, 9th Floor, Office Number 925, B.V, Doha, Qatar. Phone Number: +97433644281
[email protected]
Our Office in Kuwait city, Kuwait: Address: Sanabel Tower, 4th Floor, Office Number 411, 26 Jaber Al-Mubarak Street, Kuwait City, Kuwait. Phone Number: +96577644281
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE United Arab Emirates. Phone Number: +971 5 07204841
[email protected]
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
[email protected]
Cryptika cybersecurity office, Our office in Riyadh, Kingdom of Saudi Arabia KSA, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
[email protected]
netwrix log and event management security information and event management system social engineering becb ec-council linux foundation linux redhat fedora mandriva infrastructure security assessment debian identity management Partners in Jordan EDR Endpoint Detection and Response Security Firm EMEA Security Vendors Carbon Black EMEA Partners Carbon Black Middle East Partners Qualys Partners soc managed in amman Petya / NotPetya Ransomware zeroday zero day attacks Advanced threat protection IT Security Companies in Jordan Address: AlSwifieh Amman Jordan
[email protected]
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Cryptika Dubai UAE Amman Jordan
Middle East vendors companies providers firms mssp Cryptica Cryptika Amman Jordan
Cryptika COMPANY AMMAN JORDAN Cryptika is primarily recognized as information security firm delivering end to end comprehensive securityCryptika is the first and only Information security center and a firm and a company in Jordan amman which dedicated all its experine in cyber security and cybersecuritySecurity Solutions, Security Consultancy, Cyber Security, Cybersecurity, Information Security, NETWORKS AND INFORMATION SECURITY ENGINEERING, Security Services such penetration testing and vulnerability assessment, Vulnerability Assesment and Penetration Testing (VAPT) Service. This service enable to find vulnerabilities in network devices, application and using security, Jordan National Cyber Security Strategy
headquarters in Jordan, Cryptika operates in amman jordanCryptika is a Jordanian IT security company Specialized in information and Cyber Security, and information security. Cryptika is r in jordan and middle east, HQ based in Amman Cyber Security & Forensic Services in an event where you can gain a comprehensive insight into the agenda of the most important institutions and companies such as CryptikaThe terms information security, computer security and information assurance are on top of our services IT penetration testing Internal and external penetration tests and IT security analysis can provide those Cryptika CyberSecurity, Cyber Security, Information Security, IT Security, Penetration Testing, Vulnerability Assessment, IT Security Assessment, Security Assessment, Threat Hunting, Cryptika cybersecurity branch office in Riyadh, Address: Office 9, Oasis Center, Al Amal, Riyadh 12643, Saudi Arabia +966 5 07204841
Red Teaming
cryptika is a Jordanian Company Speciallized in Cybersecurityamman jordan xacker jaascois NAV.kill
Cryptika cybersecurity HQ in Dubai, Address: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Address 2: Office 7, Oasis Center, Sheikh Zayed Road, PO Box 128698, Dubai, UAE +971 5 07204841
Jordan central bank of jordan regulations cyber security information security ai big data
social engineering services phishing testing vishing testing service phishing testers in jordan amman security solutions network security engineer career position information security officer analyst analysis soc engineer level two three one 1 2 3 level sla service level agreement manager officer job Terms of Use Privacy Policy
Cryptika quickly earned a reputation for firsts. We were the first in region to provide our business customers with industry’s first integrated, end-to-end security operations and response services
We’re delivering a new approach in cybersecurity, purposely designed to protect your organization from the most advanced cyber-attacks. Our pioneering approach to threat hunting and response has been rigorously tested and proven by highly regarded third-party industry analysts.
..........................................................
..........................................................
امن المعلومات, امن انظمة تكنولوجيا المعلومات, الامن السيبراني
جمعان عبدالله البريكي
امن المعلومات, الامن السيبراني شركة حلول الامن السيبراني مقرنا الاردن عمان شركة اردنية متخصصة في امن المعلومات
كريبتيكا
مزود متكامل لخدمات الأمن السيبراني, أمن المعلومات, وإدارة خدمات تكنولوجيا المعلومات، مقرها دبي الامارات, الرياض المملكة العربية السعودية, عمان الأردن، تضم كريبتيكا فريقًا شاملاً من الخبراء وقادة الفكر. يشمل نطاق عملنا كل شيء بدءًا من الاستشارات والتصميم, الفحص والتقييم والتدقيق, تنفيذ وتزويد البنية التحتية لتقنية المعلومات, حلول استمرارية الاعمال الى الخدمات المُدارة ومركز عمليات أمن المعلومات المٌدار بالكامل
عمان الاردن الشرق الاوسط
البيانات اختراق عمان التحول الرقمي للتقنية شركات أمن الشبكات في الاردن في عمان مكافحة الفايروسات التحقيق الجنائي الرقمي شركات تقييم حماية المعلومات في الاردن اختبار اختراق مخترقين هاكر هاكرز فحص الثغرات الفحص الامني تدقيق داخلي تدقيق خارجي اخلاقي شهادات شهادة معتمد معتمدة معتمدون افضل شركة تكنولوجيا تقنية امن معلومات امن المعلومات امن البيانات حماية ادارة المخاطر فجوة امنية مراكز البيانات عمان مراكز العمليات الامنية شركات أمن المعلومات في الاردن شركات أمن المعلومات شركات امن المعلومات في الاردن في السعودية في الامارات في الكويت في قطر شركات امن المعلومات شركة كريبتيكا هي شركة متخصصة في الامن السيبراني وامن المعلومات وامن البيانات وامن بيئة تكنولوجيا المعلومات واختبار الاختراق وتقييم امن واستمرارية المعلومات حلول امن المعلومات حلول استمرارية المعلومات معلوماتية افضل شركة امن معلومات في الشرق الاوسط اقوى شركة عربية في الامن السيبراني وامن المعلومات هاكرزهاكر اخلاقي هاكراختبار الاختراق فحص الثغرات مراجعة الاكواد مراجعة السطور البرمجية خبراء الهندسة العكسية مهندسوا كريبتيكا الامنية المتخصصة في الامن الرقمي والتحقيق الرقمي والتحول الرقمي والجرائم الالكترونية شركة كريبتيكا لامن المعلومات مقرها الرئيسي في دبي الامارات الرياض السعودية عمان الاردن شركة امن المعلومات في الرياض عمان شركة امن المعلومات في الاردن مركز عمليات امن المعلومات خدمات مدارة حلول امن المعلومات الامن السيبراني الشركات الناشئة في تكنولوجيا المعلومات شركات تكنولوجيا المعلومات كريبتيكا للامن السيبراني امن المعلومات
دبي
الامارات
السعودية قطر
البحرين
الكويت
الاردن
عمان
الرياض
ابو ظبي
في الاردن
في دبي
في الامارات
في ابو ظبي
في السعودية
في الشرق الاوسط
في الرياض
في الكويت
الإمارات العربية المتحدة
المملكة
المملكة العربية السعودية
الإمارات العربية المتحدة
المملكة
المملكة العربية السعودية
امن المعلومات التشفير كريبتيكا البيانات اختراق عمان التحول الرقمي للتقنية شركات أمن الشبكات في الاردن في عمان مكافحة الفايروسات الصويفية شارع الوكالات التحول التحقيق الجنائي الرقمي الانتربول
شركات تقييم حماية المعلومات في الاردن شركات الانتي فايروس اختبار اختراق مخترقين هاكر هاكرز شركات السيكيوريتي في الاردن شركات فحص الثغرات الفحص الامني عقود الصيانة مستوى الخدمة تدقيق داخلي تدقيق خارجي اخلاقي شهادات شهادة معتمد معتمدة معتمدون افضل شركة تكنولوجيا
تقنية امن معلومات امن المعلومات امن البيانات حماية استرجاع احتياطية ادارة المخاطر فجوة امنية مراكز البيانات عمان مراكز العمليات الامنية
شركات أمن المعلومات في الاردن
شركات أمن المعلومات
شركات امن المعلومات في الاردن
شركات امن المعلومات
شركة كريبتيكا هي شركة متخصصة في الامن السيبراني وامن المعلومات وامن البيانات وامنة بيئة تكنولوجيا المعلومات واختبار الاختراق وتقييم امن واستمرارية المعلومات حلول امن المعلومات حلول استمرارية المعلومات معلوماتية
افضل شركة امن معلومات في الشرق الاوسط
اقوى شركة عربية في الامن السيبراني وامن المعلومات
مخترقون
هاكرز
هاكر اخلاقي
هاكر
اختبار الاختراق فحص الثغرات مراجعة الاكواد مراجعة السطور البرمجية خبراء الهندسة العكسية مهندسوا كريبتيكا الامنية المتخصصة في الامن الرقمي والتحقيق الرقمي والتحول الرقمي والجرائم الالكترونية
شركات تكنولوجيا المعلومات
كريبتيكا للامن السيبراني
تأمين استمرارية الأعمال
حلول استمرارية الاعمال
حلول توافر البيانات
تامين تكنولوجيا المعلومات
شركات تأمين أمن المعلومات في الشرق الأوسط
الفريق العربي للبرمجة منتديات العاصفة اختراق العرب الهاكرز تعليمات البنك المركزي الاردني في امن البيانات المالية المعلومات المالية المحاسبة
الإمارات العربية المتحدة
المملكة
المملكة العربية السعودية
الإمارات العربية المتحدة
المملكة
المملكة العربية السعودية
الإمارات العربية المتحدة
المملكة
المملكة العربية السعودية
الإمارات العربية المتحدة
المملكة
المملكة العربية السعودية
اختراق التطبيقات
تجارب اختراق تطبيقات
امن المعلومات
شركة امن معلومات الاردن في الاردن شركة امن سيبراني الاردن في عمان شركات امن المعلومات في عمان شركات أمن المعلومات في الاردن
الفريق العربي للبرمجة منتديات العاصفة اختراق العرب الهاكرز العربي الفريق العربي شركات عربية في امن المعلومات مجال امن البيانات مجال الامن السيبراني تعليمات البنك المركزي الاردني في امن البيانات المالية المعلومات المالية المحاسبة
اصطياد التهديدات المخاطر صائدوا التهديدات منصة صيد المخاطر صيد التهديدات منصات صيد المخاطر والتهديدات خدمة اختبار الاختراق الاخلاقي بالاردن مخترق اخلاقي فحص تقييم الثغرات حجوم حجب الخدمة
كريبتيكا!. مزود متكامل لخدمات الأمن السيبراني, أمن المعلومات, وإدارة خدمات تكنولوجيا المعلومات، مقرها في الأردن، تضم كريبتيكا فريقًا شاملاً من الخبراء وقادة الفكر. يشمل نطاق عملنا كل شيء بدءًا من الاستشارات والتصميم, الفحص والتقييم والتدقيق, تنفيذ وتزويد البنية التحتية لتقنية المعلومات, حلول استمرارية الاعمال الى الخدمات المُدارة ومركز عمليات أمن المعلومات المٌدار بالكامل